Curriculum Information
0. Cover, Checklist
1. Vocab
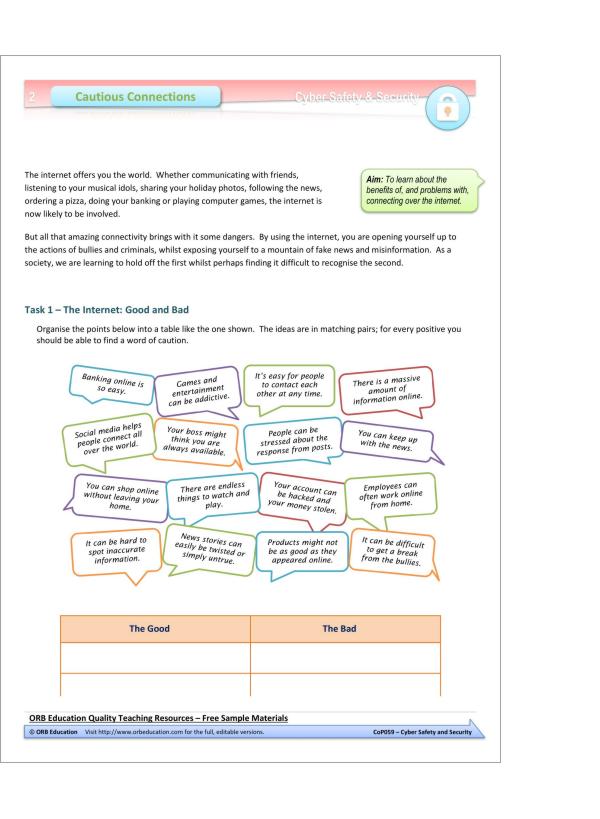
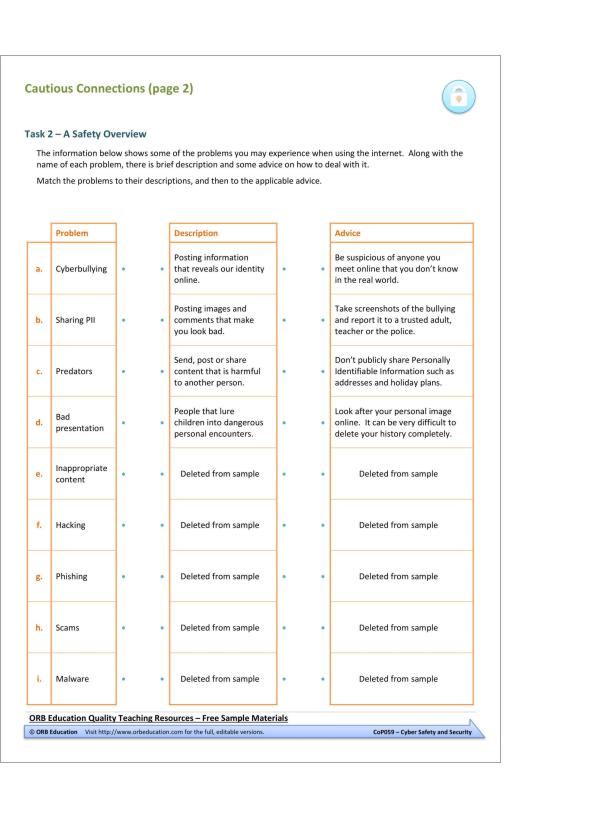
2. Cautious Connections
NSW Comp Tech (2024)-Net: ¤ Specify the non-functional requirements of a networked solution: Social benefit or facilitating social interactions.
3. Cyberbullying
“NSW DT(Tech Mand): LS – · explore social and ethical issues associated with digital solutions, for example:
– cyber safety
– appropriate digital communicationNSW Comp Tech (2024)-Net: ¤ Explore how people’s changing expectations and concerns for security and privacy have shaped computer technology: Identity verification of social media profiles, such as considering cyber safety before connecting with someone on social media. ”
4. Passwords
AC V9.0 (Recap 5-6): – using multiple accounts, each with different passphrases, to access each website or app used for school and home, for example having a different username and password combination for school, gaming and music accounts
AC V9.0 (Recap 5-6): – explaining why re-using a password is risky when one of them is found out, for example how a compromised password from one social media account might be able to be used to access their bank or school account if the password is the same and other details are also compromised
AC V9.0 (7-8): · explain how multi-factor authentication protects an account when the password is compromised … (AC9TDI8P13)
AC V9.0 (7-8): – explaining how multi-factor authentication prevents unauthorised access by prompting the account owner for a token or single-use password, for example demonstrating how a funds transfer from their bank account requires not only logging in, but provision of a one-time password received via SMS
AC V9.0 (7-8): Investigate personal security controls, including multi-factor authentication, to protect their data if passwords are compromised…
5. Your Personal Data
6. Big Data
AC V9.0 (7-8):
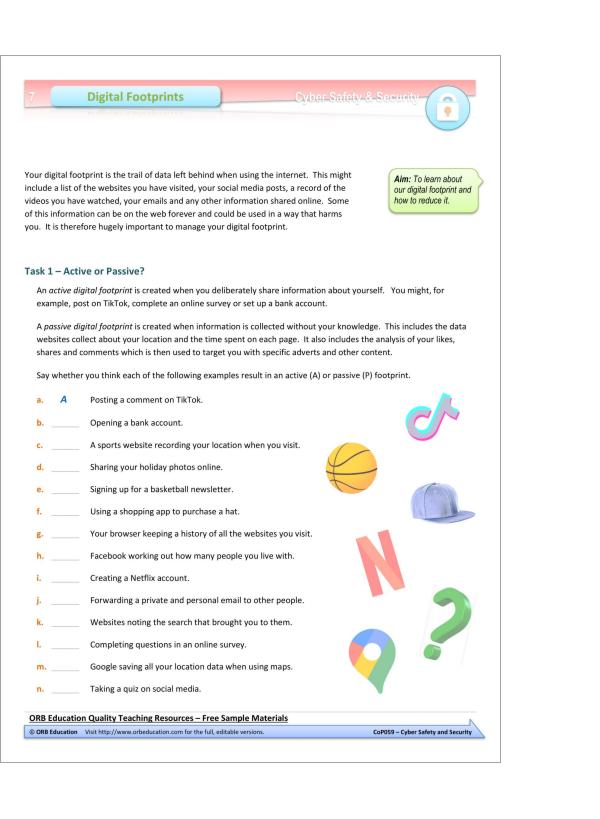
7. Digital Footprint
AC V9.0 (Recap 5-6): – describing scenarios where data, images or both that have been posted online can lead to information being resurfaced at a later date, for example how a comment made on a social media post or video associates a person with both their comment and the content
AC V9.0 (Recap 5-6): Identify their digital footprint and recognise its permanence.
AC V9.0 (7-8): Manage their digital footprint.
AC V9.0 (7-8): · investigate and manage the digital footprint existing systems and student solutions collect and assess if the data is essential to their purpose (AC9TDI8P14)
AC V9.0 (7-8): – reviewing and managing their digital footprint across online digital tools that they use, for example selecting their default privacy and sharing settings on social media accounts
8. Data Privacy
AC V9.0 (7-8): – assessing the appropriateness and relevance of data collected by surveys from other students and organisations they complete online, for example identifying that providing your address data is not necessary for a survey asking about your food preferences but providing the address for the Census would be appropriate
AC V9.0 (7-8): – investigating the ethical obligations of individuals and organisations regarding ownership and privacy of data and information by researching an online platform’s privacy policy for data collection, use and storage information and discussing impacts on digital footprint
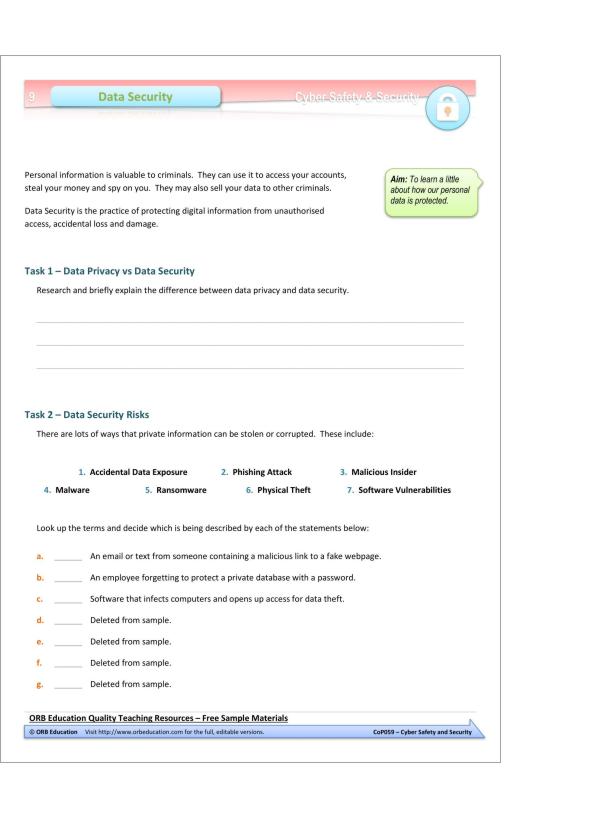
9. Data Security
AC V9.0 (7-8): Investigate personal security controls… and they understand the impact of phishing and other cyber security threats on people and data.
10. Securing Your Data
NSW Comp Tech (2024)-Net: ¤ Evaluate the social impacts and ethical and legal responsibilities in connecting people and systems: … protecting personally identifying information (PII).
NSW Comp Tech (2024)-Net: ¤ selects and applies safe, secure and responsible practices in the ethical use of data and computing technology NSW Comp Tech (2024)5-SAF-01:
11. Collaboration
AC V9.0 (Recap 5-6): – defining and acting collectively using online community standards and valuing the work of others, for example moderating language and behaviour in an online class forum, not deleting the work of collaborators, and respecting others’ intellectual propertyNSW DT(Tech Mand): LS – – collaboration
AC V9.0 (Recap 5-6): Select and use appropriate digital tools effectively to plan, create, locate and share content, and to collaborate, applying agreed conventions and behaviours.
AC V9.0 (7-8): – collaborating effectively online using cloud storage, for example setting up and managing a shared space in an online repository…
AC V9.0 (7-8): Select and use a range of digital tools efficiently and responsibly to create, locate and share content; and to plan, collaborate on and manage projects.
AC V9.0 (7-8): – determining and recording the tasks, responsibilities and timeframes for a collaborative project, for example using a spreadsheet to record tasks and their sequence, critical dates and who is responsible for each task so a project can be finished on time
12. Encryption
AC V9.0 (7-8): – exploring simple encryption and decryption algorithms, for example ROT13 and XOR
13. Encryption Spreadsheets
14. Copyright
NSW DT(Tech Mand): – copyright and intellectual property
15. Accessibility
NSW DT(Tech Mand): – accessibility
By Curriculum
Australian Curriculum V9.0 (2024)
AC V9.0 (Recap 5-6): · access multiple personal accounts using unique passphrases and explain the risks of password re-use (AC9TDI6P09)
AC V9.0 (Recap 5-6): – using multiple accounts, each with different passphrases, to access each website or app used for school and home, for example having a different username and password combination for school, gaming and music accounts
AC V9.0 (Recap 5-6): – explaining why re-using a password is risky when one of them is found out, for example how a compromised password from one social media account might be able to be used to access their bank or school account if the password is the same and other details are also compromised
AC V9.0 (7-8): · explain how multi-factor authentication protects an account when the password is compromised … (AC9TDI8P13)
AC V9.0 (7-8): – explaining how multi-factor authentication prevents unauthorised access by prompting the account owner for a token or single-use password, for example demonstrating how a funds transfer from their bank account requires not only logging in, but provision of a one-time password received via SMS
AC V9.0 (7-8): Investigate personal security controls, including multi-factor authentication, to protect their data if passwords are compromised…
AC V9.0 (7-8): – investigating how recommendation algorithms used in media services rely on data that tracks user habits, for example how music streaming services generate playlists that contain songs from genres and artists that are similar to those you listen to regularly
AC V9.0 (7-8):
AC V9.0 (Recap 5-6): · explain the creation and permanence of their digital footprint and consider privacy when collecting user data (AC9TDI6P10)
AC V9.0 (Recap 5-6): – describing scenarios where data, images or both that have been posted online can lead to information being resurfaced at a later date, for example how a comment made on a social media post or video associates a person with both their comment and the content
AC V9.0 (Recap 5-6): Identify their digital footprint and recognise its permanence.
AC V9.0 (7-8): Manage their digital footprint.
AC V9.0 (7-8): · investigate and manage the digital footprint existing systems and student solutions collect and assess if the data is essential to their purpose (AC9TDI8P14)
AC V9.0 (7-8): – reviewing and managing their digital footprint across online digital tools that they use, for example selecting their default privacy and sharing settings on social media accounts
AC V9.0 (Recap 5-6): – explaining why collecting the smallest amount of data needed for a purpose is important to protect someone’s privacy, for example how choosing not to collect information about someone’s birthdate when it is not necessary ensures that private data cannot be stolen in a cyber attack
AC V9.0 (7-8): – assessing the appropriateness and relevance of data collected by surveys from other students and organisations they complete online, for example identifying that providing your address data is not necessary for a survey asking about your food preferences but providing the address for the Census would be appropriate
AC V9.0 (7-8): – investigating the ethical obligations of individuals and organisations regarding ownership and privacy of data and information by researching an online platform’s privacy policy for data collection, use and storage information and discussing impacts on digital footprint
AC V9.0 (7-8): · … identify phishing and other cyber security threats (AC9TDI8P13)
AC V9.0 (7-8): Investigate personal security controls… and they understand the impact of phishing and other cyber security threats on people and data.
AC V9.0 (7-8): – identifying the common techniques used in phishing scams to identify and exploit susceptible users, for example using an email address from an unofficial domain when pretending to be an online retailer, or including grammatical errors to help filter out users who are more likely to detect the scam
AC V9.0 (Recap 5-6): Explore different ways of working collaboratively, such as agreeing on how tasks should be allocated and content shared.
AC V9.0 (Recap 5-6): – defining and acting collectively using online community standards and valuing the work of others, for example moderating language and behaviour in an online class forum, not deleting the work of collaborators, and respecting others’ intellectual property
AC V9.0 (Recap 5-6): Select and use appropriate digital tools effectively to plan, create, locate and share content, and to collaborate, applying agreed conventions and behaviours.
AC V9.0 (7-8): – collaborating effectively online using cloud storage, for example setting up and managing a shared space in an online repository…
AC V9.0 (7-8): Select and use a range of digital tools efficiently and responsibly to create, locate and share content; and to plan, collaborate on and manage projects.
AC V9.0 (7-8): – determining and recording the tasks, responsibilities and timeframes for a collaborative project, for example using a spreadsheet to record tasks and their sequence, critical dates and who is responsible for each task so a project can be finished on time
AC V9.0 (7-8): – explaining why cryptography is necessary for securing data, for example transmitting credit card details over the internet
AC V9.0 (7-8): – exploring simple encryption and decryption algorithms, for example ROT13 and XOR
NSW Digital Technologies (Tech Mandatory)
NSW DT(Tech Mand): LS – – applying safe practices when communicating online
NSW DT(Tech Mand): · identify social, ethical and cyber security considerations of digital solutions, for example:
NSW DT(Tech Mand): LS – – appropriate digital communication
NSW DT(Tech Mand): – privacy issues and digital footprints
NSW DT(Tech Mand): LS – – managing privacy settings when using social media
NSW DT(Tech Mand): LS – · explore social and ethical issues associated with digital solutions, for example:
NSW DT(Tech Mand): LS – · evaluate their design and production skills, for example: DT
NSW DT(Tech Mand): LS – – collaboration
NSW DT(Tech Mand): LS – – copyright when using online images and media
NSW DT(Tech Mand): – copyright and intellectual property
NSW DT(Tech Mand): LS – – accessibility of online content
NSW DT(Tech Mand): – accessibility
NSW Computing Technology (2024)
NSW Comp Tech (2024)-Net: ¤ Describe the purpose of connecting people and systems:
NSW Comp Tech (2024)-Net: ¤ Specify the non-functional requirements of a networked solution: Social benefit or facilitating social interactions.
NSW Comp Tech (2024)-Net: ¤ Evaluate the social impacts and ethical and legal responsibilities in connecting people and systems: Social: online access to services, remote working, cyber bullying, or the filter bubble.
NSW Comp Tech (2024)-Net: ¤ Explore how people’s changing expectations and concerns for security and privacy have shaped computer technology: Identity verification of social media profiles, such as considering cyber safety before connecting with someone on social media.
NSW Comp Tech (2024)-Data: ¤ Explore design principles and issues relevant to analysing data, including visualisation principles, data trails and ownership of data: Accessing and restricting your historical data or tracking users to customise advertising with browser cookies.
NSW Comp Tech (2024)-Net: ¤ Specify what data is collected, who owns it, and how it will be protected, considering privacy and cybersecurity, including when interpreting data:
NSW Comp Tech (2024)-Net: ¤ Evaluate the social impacts and ethical and legal responsibilities in connecting people and systems: Legal: reporting data breaches to users and regulators, anonymising data and disposal of PII.
NSW Comp Tech (2024)-Net: ¤ Evaluate solutions against the predetermined functional and non-functional requirements that meet social, ethical and legal responsibilities and cybersecurity principles:
NSW Comp Tech (2024)-Net: ¤ Explore how people’s changing expectations and concerns for security and privacy have shaped computer technology: Using appropriate firewall settings, such as implementing cyber security to browser software.
NSW Comp Tech (2024)-Net: ¤ Evaluate the social impacts and ethical and legal responsibilities in connecting people and systems: Ethical: black-hat and white-hat hacking, Digital Literacy codes of conduct, or protecting personally identifying information (PII).
NSW Comp Tech (2024)-Net: ¤ selects and applies safe, secure and responsible practices in the ethical use of data and computing technology NSW Comp Tech (2024)5-SAF-01:
NSW Comp Tech (2024)-UE: ¤ manages, documents and explains individual and collaborative work practices NSW Comp Tech (2024)5-COL-01:
NSW Comp Tech (2024)-Data: ¤ Investigate issues with the use of data, including cyber safety, security, privacy and ethics: Breach of copyright.
NSW Comp Tech (2024)-Net: ¤ Investigate how the profile and attributes of end users are used by developers when creating products: Accessibility needs, such as vision and hearing.






Reviews
There are no reviews yet.